An extension of its HP Secure Advantage portfolio announced the summer of 2006, HP Secure Print Advantage encrypts documents at the point of printing with a client module, inspects each sent job for malware, and then terminates the job if infected or re-encrypts it and delivers it to a secure print module if clean.
- Oct 18 Thu 2007 11:01
HP Attacks the Printer Security Gap
Hewlett Packard on Oct. 17 introduced HP Secure Print Advantage, an appliance-software combination that attempts to wall off from the network an often-forgotten but growing attack vector—the printer.
An extension of its HP Secure Advantage portfolio announced the summer of 2006, HP Secure Print Advantage encrypts documents at the point of printing with a client module, inspects each sent job for malware, and then terminates the job if infected or re-encrypts it and delivers it to a secure print module if clean.
An extension of its HP Secure Advantage portfolio announced the summer of 2006, HP Secure Print Advantage encrypts documents at the point of printing with a client module, inspects each sent job for malware, and then terminates the job if infected or re-encrypts it and delivers it to a secure print module if clean.
- Oct 18 Thu 2007 10:52
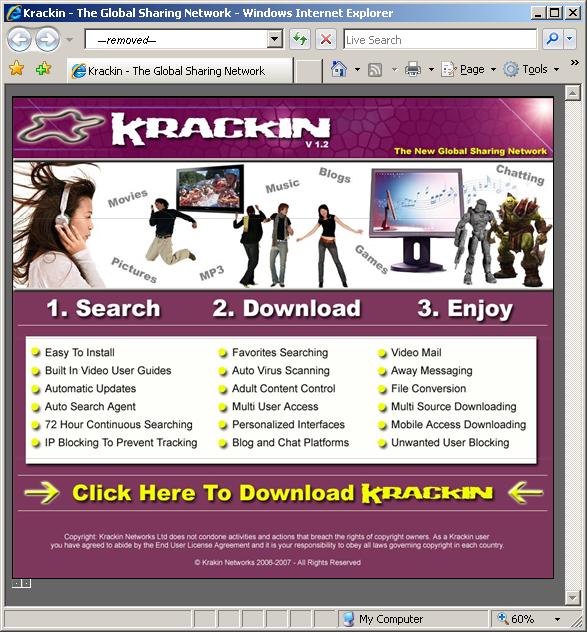
The New Global Storming Network
A new Storm site advertises a networking application. That site looks like this:

- Oct 18 Thu 2007 10:51
Skype Stealer
Yesterday we added detection for a Trojan-Spy password stealer targeting Skype. The malware bills itself as Skype Defender, which sounds like a security plug-in.
Running the malware produces this dialog:
Running the malware produces this dialog:
- Oct 18 Thu 2007 10:40
Metasploit adds iPhone/iPod Touch hacks
As reported in ComputerWorld, security researcher H.D. Moore has included several iPhone and iPod Touch exploits in the latest Metasploit tool. The free tool is used by professional pen-testers and criminal hackers alike. The new exploits take advantage of a flaw in the TIFF image-rendering library and are similar to flaws used by the iPhone Dev Team.
"This exploit is rock solid. It's very reliable, as reliable as the WMF [Windows Metafile] exploits in Windows. You can send it in an e-mail; you can embed it in a Web page," Moore told ComputerWorld.
"This exploit is rock solid. It's very reliable, as reliable as the WMF [Windows Metafile] exploits in Windows. You can send it in an e-mail; you can embed it in a Web page," Moore told ComputerWorld.
- Oct 18 Thu 2007 10:37
Congress concerned P2P promotes identity theft, calls for federal investigation
Still worried that peer-to-peer filesharing networks like Lime Wire are causing users to "inadvertently" expose sensitive documents, posing potential security risks, members of Congress are now asking for a formal investigation into the phenomenon.
The latest concern from the House of Representatives Committee on Oversight and Government Reform, judging by a 7-page letter (click for PDF) dated Wednesday to Federal Trade Commission chairwoman Deborah Majoras, appears to be this: Peer-to-peer networks may make unsuspecting consumers vulnerable to identity theft.
The latest concern from the House of Representatives Committee on Oversight and Government Reform, judging by a 7-page letter (click for PDF) dated Wednesday to Federal Trade Commission chairwoman Deborah Majoras, appears to be this: Peer-to-peer networks may make unsuspecting consumers vulnerable to identity theft.
- Oct 17 Wed 2007 11:20
Core Security Adds Web App Testing to Tool Belt
Core Security Technologies is adding Web application penetration testing to the latest version of its security assurance tool.
Set to be released within 30 days, Core Impact Version 7.5's new abilities mark an increased recognition of the vulnerabilities affecting Web applications by the Boston-based firm, which started out focusing on testing of network servers and services before branching out to cover client-side attacks.
Set to be released within 30 days, Core Impact Version 7.5's new abilities mark an increased recognition of the vulnerabilities affecting Web applications by the Boston-based firm, which started out focusing on testing of network servers and services before branching out to cover client-side attacks.
- Oct 17 Wed 2007 11:17
Oracle Issues Pile of 51 Security Patches
Oracle on Oct. 16 released 51 security fixes, including 27 patches for the beating heart of so many enterprises: the Oracle database.
In addition to that load of patches, Oracle administrators can also look forward to rolling out 11 patches to Oracle's Application Server, seven to Oracle Collaboration Suite, eight to Oracle E-Business Suite and Applications, three to Oracle Enterprise Manager and three to Oracle PeopleSoft Enterprise and JD Edwards EnterpriseOne.
In addition to that load of patches, Oracle administrators can also look forward to rolling out 11 patches to Oracle's Application Server, seven to Oracle Collaboration Suite, eight to Oracle E-Business Suite and Applications, three to Oracle Enterprise Manager and three to Oracle PeopleSoft Enterprise and JD Edwards EnterpriseOne.
- Oct 17 Wed 2007 11:10
[轉貼]$1M in Damages? Impact of Security Breaches Gets Worse
There are fewer security breaches, but they're getting worse.
That's the message of a new report from CompTIA , an IT industry association. To respond to the heightened risk, companies are spending more money on security technology. Security rose to 20% of IT budgets in 2006, compared to 15% in 2005 and 12% in 2004, CompTIA says.
That's the message of a new report from CompTIA , an IT industry association. To respond to the heightened risk, companies are spending more money on security technology. Security rose to 20% of IT budgets in 2006, compared to 15% in 2005 and 12% in 2004, CompTIA says.
- Oct 17 Wed 2007 11:03
[轉貼]Security expert: Storm botnet 'services' could be sold
The owners of the Storm botnet, whose identities are as yet unknown, could be preparing to sell off the "services" of segments of the
network, according to Joe Stewart, a researcher from managed security services company SecureWorks.
network, according to Joe Stewart, a researcher from managed security services company SecureWorks.
- Oct 17 Wed 2007 10:57
New Software Flaws Affect Nearly Every Windows User
SANS reports nearly 100 new flaws in commercial software this week; thousands more are found in custom software.
As of yesterday, the four most critical flaws affect Internet Explorer, Outlook Express, Microsoft Word, and Kodak Image Viewer, which Microsoft patches because it comes with Windows.
As of yesterday, the four most critical flaws affect Internet Explorer, Outlook Express, Microsoft Word, and Kodak Image Viewer, which Microsoft patches because it comes with Windows.
- Oct 15 Mon 2007 10:04
[轉貼]淺談web app二次漏洞
在假設設計上不存在問題(即人解決某個應用的方式不存在問題)以及改採用的語言以及其他周邊組件是安全的情況下,程序的漏洞就大部分就是由於在實現問題的過程中,程序員對安全的漠視或是對安全的不太瞭解造成的,而從程序的角度看,這種漏洞不外乎是不安全的參數進入不安全的操作中引起的。
不安全的操作大家都知道有很多,譬如文件讀寫,數據庫查詢,代碼執行以及其他的一些危險函數的使用等等,那麼不安全的參數主要是哪些呢?有人說所有用戶的輸入都是有害的,在我看來輸入可以分兩種,直接的輸入與間接的輸入。直接的輸入是可以看到的,如url裡的參數,瀏覽器與服務器的一些環境變量,用戶提交的Cookie,用戶通過表單進行的輸入等等,對於這些輸入大部分的程序員都會在安全上比較在意,比較注意參數的過濾,因為這些輸入是顯而易見的,觸發比較簡單,甚至一些輸入如果不做過濾的話會導致程序出錯,再加上PHP這種語言對於一些進入的參數的默認保護(Magic Quote選項),所以這種參數現在在大的程序裡比較少出問題,但是另外一種隱式的輸入卻被人們忽略了,那就是來自數據庫(包括Mysql這種數據庫,文本數據庫和一些人常用的cache以及php配置文件等等),可以嘗試為程序做一個流程圖:
不安全的操作大家都知道有很多,譬如文件讀寫,數據庫查詢,代碼執行以及其他的一些危險函數的使用等等,那麼不安全的參數主要是哪些呢?有人說所有用戶的輸入都是有害的,在我看來輸入可以分兩種,直接的輸入與間接的輸入。直接的輸入是可以看到的,如url裡的參數,瀏覽器與服務器的一些環境變量,用戶提交的Cookie,用戶通過表單進行的輸入等等,對於這些輸入大部分的程序員都會在安全上比較在意,比較注意參數的過濾,因為這些輸入是顯而易見的,觸發比較簡單,甚至一些輸入如果不做過濾的話會導致程序出錯,再加上PHP這種語言對於一些進入的參數的默認保護(Magic Quote選項),所以這種參數現在在大的程序裡比較少出問題,但是另外一種隱式的輸入卻被人們忽略了,那就是來自數據庫(包括Mysql這種數據庫,文本數據庫和一些人常用的cache以及php配置文件等等),可以嘗試為程序做一個流程圖:
- Oct 15 Mon 2007 09:55
Bringing Security into the Development Process
When it comes to data leaks, most of the talk is about hackers breaking into networks or employees e-mailing and downloading sensitive information. But some vendors are paying more attention to the preproduction environment, where there are often security holes big enough to push a hard drive through.
"The development environment and quality assurance environment have always been…significantly more open and free," said Louis Carpenito, former vice president of information security business strategy at Symantec.
"The development environment and quality assurance environment have always been…significantly more open and free," said Louis Carpenito, former vice president of information security business strategy at Symantec.
- Oct 15 Mon 2007 09:51
E-Bay of Zero-Day Bugs Plans Expansion
WabiSabiLabi made a bit of a scene when officials there announced they created a marketplace for security researchers to hawk their findings to the highest bidder.
Roughly two months after its creation, company officials are touting what they say is the success of their marketplace, which has had some 160,000 unique visitors, and is looking to expand.
Roughly two months after its creation, company officials are touting what they say is the success of their marketplace, which has had some 160,000 unique visitors, and is looking to expand.
- Oct 15 Mon 2007 09:28
Bug fixed in Flickr-to-Twitter code?
There was definitely a bug in the code that processed Flickr categories in Twittergram. If you'd specify that a picture required a tag, and one of the pictures didn't have it, all the other new pictures would be ignored, whether they had the tag or not. Permalink to this paragraph
Some people who used the category tagging feature didn't notice this problem because they never uploaded pictures without the tags. Permalink to this paragraph
Some people who used the category tagging feature didn't notice this problem because they never uploaded pictures without the tags. Permalink to this paragraph
- Oct 12 Fri 2007 15:42
[大砲開講]HiNet理財網又被植入惡意連結
HiNet理財網又被植入惡意連結,此惡意程式為 Trojan-PSW.Win32.OnLineGames
.dzq
,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒。(Credit: Jimau)

